 My last blog I dedicated to the availability of the integration of the Microsoft Intune and Lookout Mobile Threat Protection cloud services.
My last blog I dedicated to the availability of the integration of the Microsoft Intune and Lookout Mobile Threat Protection cloud services.
So have this time have a look at the architecture of the integration, before writing about how to set everything up, the administrative and the end-user experience.
Introduction
Currently Microsoft Intune is hosted on Microsoft Azure and Lookout Mobile Threat Protection is hosted on Amazon Web Services. Microsoft Intune is still a fairly closed platform that currently has no public API that the different vendors and partners can use to interact with Microsoft Intune. PowerShell support for instance is for Intune is part of the plans of the Intune product group. (vote on User Voice)
For the integration with Lookout Microsoft created an Intune API especially for Lookout.
The architecture of the Integration
When the Intune and Lookout MTP tenants are “connected” Lookout MTP is able to gather user and device ID information from Azure Active Directory via the Microsoft Intune connector. Also Lookout MTP is federated with Azure Active Directory so that Single Sign On to the Lookout service is provided.
If a threat is detected Lookout MTP is able to share the threat level with Intune and based on the compliance policy, the user is allowed conditional access will allow or not allow access to for instance Office 365.
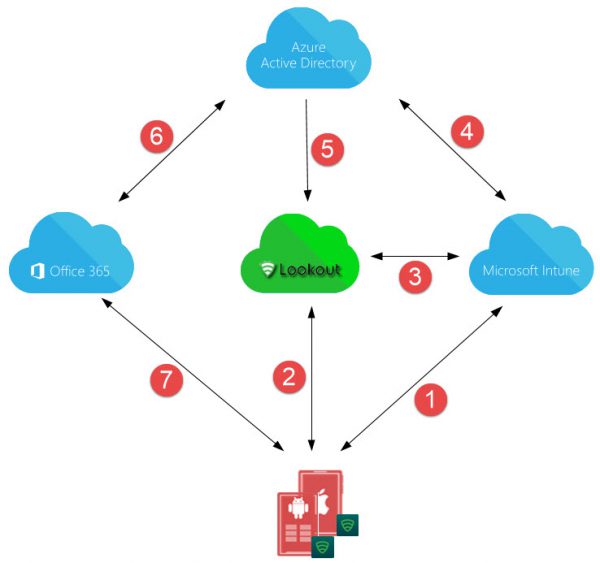
Looking at the figure below we will see how the services work together.
- The Device is enrolled in and managed by Microsoft Intune.
- Lookout for Work client is connected with Lookout service and reports device state. If threat is detected it will be reported to the Lookout service.
- Information about the state of the device is shared between Intune and Lookout. If a threat is detected by lookout this is shared with Intune and checked if the compliance policy is configured to block or allow the threat level.
- Intune shares the compliance state in Azure AD, based on the threat level. Devices managed with Intune are also registered in Azure AD.
- Lookout gets device state and information from Azure AD (via Intune connector). Also Lookout is federated with Azure AD. In case of a threat the device compliance state is changed in Intune (via connection 3) and shared in Azure AD (via connection 4).
- Office 365 gets device compliance state of Azure AD.
- If compliant, access to Office 365 is permitted, if not access will be blocked.
The Intune versus Lookout connector
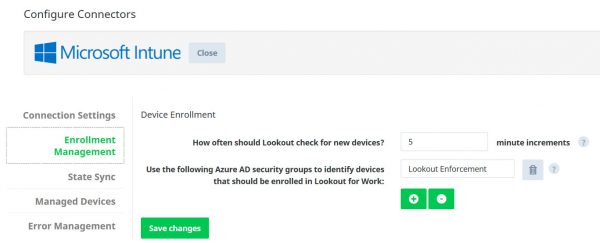
After setting up the connection between Azure AD and Lookout via OAuth, every X number of minutes new devices will be discovered based on the users that are a member of one or more Azure AD security groups.
Compliance state
The compliance level of the device is determined by the following controls;
| State Device / Lookout | Compliance state |
| Lookout for Work not installed | Not compliant |
| Lookout for Work not activated via AAD | Not compliant |
| Threat detected (None,Low, Med, High) | Not compliant, based on compliance setting in Intune. Medium threat level needs to be configured.
This medium threat level can be None (secure), Low, Medium or High. |
I my next blog we will have a look at how to setup the connection between Lookout and Microsoft Intune.
Stay tuned!
Want to see the integration in action?
At IT/Dev Connections (10/10 10/13) I will show the same during at our full day Microsoft Enterprise Mobility +Security workshop ; How You Can Digitally Transform Any Organization on Monday! Be sure to join Kenny Buntinx, Tim De Keukelaere and me in Las Vegas, there are still tickets available!
Other blogs in this series:
- Integration Microsoft Intune and Lookout Mobile Threat Protection is there
- Intune and Lookout: the architecture of the integration
- Intune and Lookout: how to integrate?
- Intune and Lookout: the admin experience.
- Intune and Lookout: the end user experience.
- Intune and Lookout: supporting iOS devices
- Intune, ConfigMgr and Lookout better together